You may hear the terms Cybersecurity or Network Security assessment; these terms are very similar and depending on who you talk to they may use the terms interchangeably. Cybersecurity is defined to cover your Cloud networks outside of your offices network.
In today’s world cyber-attacks are occurring it seems only daily. The attack is one event, but the compromise is what you do not want occurring. In 2021 there have been compromises that have occurred that have made the news. Chances are if you have a compromise, you may not make the news, but you may lose some customers or have to go out of business because the costs are too great.
Two big recent events that have occurred and we felt the impact were: the Colonial Pipeline (disrupted fuel supply in the US) and JBS (disrupted our food supply).
You may never prevent a compromised 100%, but you can reduce your chances of becoming a statistic or if a compromise occurs you recover quickly.
The first step is to get a comprehensive security assessment this will help uncover the “low hanging fruit” and often fills the most common gaps. Most attackers are looking for the easy targets, these are often small to medium sized businesses.
A good assessment is not something done in a few hours, it can take several days’ worth of work on behalf of the security assessor.
Do I need a security assessment?
Most industries do not require any type of security assessment, but if you answer yes to one of these questions, you should probably have an assessment done:
- Do you accept or input credit card information (PCI Compliance)
- Are you a healthcare related company, dental, medical, provide software, etc. (HIPAA Compliance)
- Do you maintain healthcare records of any individuals, example HR and workers comp claims (HIPAA Compliance)
- Do work with State, Local, or the Federal government (part of an assessment)
DK Systems can help with your cybersecurity/network security assessment. Call today 414-764-4465 to discuss.
More information about a cybersecurity assessment
The rest of this post is to provide information and define different areas of what an assessment involves.
Gone are the days when the owner of a company could maintain the computers in the office. Today’s networks require updated technology and techniques to help keep the bad actors out.
Pressure from the Federal government has increased since the two attacks mentioned occurred. The Federal Government is requiring contractors and sub-contractors perform security assessment show proof of it. Not just saying they are meeting the requirements.
Difference between an attack and a compromise
Attacks occur everyday against a company firewall; many people just do not realize it because the attacks are hidden and not reported unless you have a system in place to do so. For example, our mail server blocks IPs after X number of failed attempts, here is a snapshot:
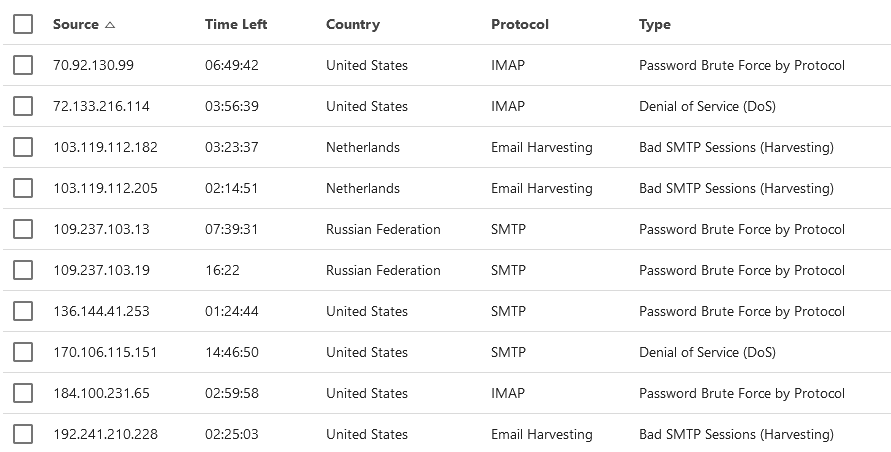
You can see people from all over are trying to break into systems. This is a low number there are often blocked attempts from China and a few other countries. These screenshots are just to show our mail customers have no idea of the attacks occurring.
This is an example of what my honeypot has blocked, some days the numbers are greater than others.
Sample 1 shows IPs that did a basic scan against my network, note the 671:
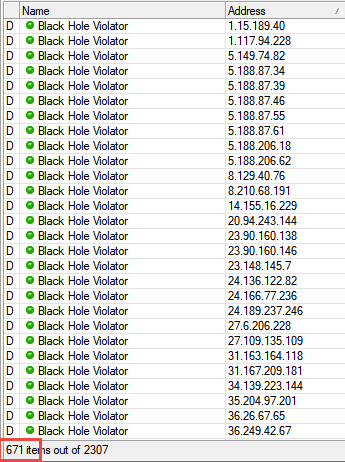
Sample 2:
The following list is a honey pot for potential Spammers, this cuts down on the number of report IPs on my server.
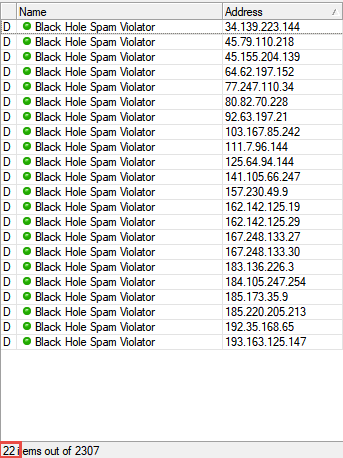
This information is just provided so you understand attacks are occurring all the time, a compromise is when the attack is successful, this is what you want to avoid.
What can happen during a compromise?
The effects of an attack/compromise can vary. The most common today is Ransomware. A Ransomware attack locks all of your files, sometimes a threat of exposing your data. To get your files back you often need to pay a ransom of bit coins. Just because you pay the ransom there is no guarantee you will get your files back. The FBI warns against paying the ransom, this only encourages more of these types of attacks. Your best bet is to recover from a good backup.
What is included in a security assessment?
This varies between assessors, but the basics include:
- A map/list of all your IT related devices
- A list of potential non-IT related risks and their impact, an example you do not have a lock on the front door.
- Gaps found in your IT network broken down by device
- A checklist of what needs to be done to remediate the gaps found
- Summary/executive summary of your company’s IT security health
What is a penetration test or pen test?
A penetration test or pen test, is assessor attempting to break into a company network, they utilize many of the same tools a hacker would use. Very often this is not a true test of a security assessment because most pen testers can get in somehow. DK Systems will do some penetration tests, but we bring in a 3rd party as an independent assessor. We focus on finding and closing gaps and the 3rd party follow-up.
How does DK Systems approach your security assessment?
DK Systems uses an approach/technique that common practice of security professionals. It is referred to as defense in layers. Defense in layers is an approach that reduces risk by placing multiple barriers in the way of an attacker. You may not realize it, but you do a defense in layer to keep your home safe.
Here is an example with a comparison between your home and your office network:
| Threat | Solution | ||
| Your Home | Your Network | Home | Network |
| Walking in | Connect remotely | Fence/doors/windows | Firewall |
| Open a door | Use a computer | Locks | Password |
| Break-in occurred | Alarm | Intrusion Detection | |
| Fire | Virus/malware | Smoke detector | Antivirus software |
This is just a small comparison to give you an idea of what defense in layers is.
Most common causes of compromises
- Misconfigured computers or other networking equipment
- Missing patches
- Users with excessive permissions
- Untrained users in cybersecurity best practices